Previous Posts
Websense Security Labs has discovered that Google’s popular web mail service Gmail is being targeted in recent spammer tactics. Spammers in these attacks managed to created bots that are capable of signing up and creating random Gmail accounts for spamming purposes.
Websense believes that from the spammers’ perspective, there are four main advantages to this approach. First, signing up for an account with Google allows access to its wide portfolio of services. Second, Google’s domains are unlikely to be blacklisted. Third, they are free to sign up. And fourth, it may be hard to keep track of them as millions of users worldwide are using various Google services on a regular basis.
Gmail, called Google Mail in Germany, Austria and the United Kingdom, is a free Web-based email (webmail), POP3 and IMAP e-mail service provided by Google. It was released on April 1, 2004 as a private beta release by invitation only and was opened to all as a public beta on February 7, 2007. With an initial storage capacity of 1 GB, it dramatically increased the standard for free storage.
Gmail currently offers over 6000 MB of free storage with an additional 10 GB available for US$20 per year. Gmail is well-known for its simplicity and flexibility, its user-friendly design; and has tens of millions of users globally.
Screenshots showing Gmail accounts being signed on compromised machines:
Screenshots showing the spammer accounts created:
Websense believes that these accounts could be used by spammers at any time for abusing Google’s infrastructure. A wide range of attacks could be possible as the same account credentials can be used to target various services offered by Google.
Analysis report
It is observed that at this stage bots (or bot-infected machines) are trying to sign up as many accounts as possible with Gmail mail services. One of the main concerns here is attacking CAPTCHA. Unfortunately, spammers seem to have success with it. The bot is signing up an account feeding all the prerequisites or input data that goes into the signup page and successfully creating a mail account.
Considering the normal / routine process involved in signing up a web mail account (Gmail), CAPTCHA authentication is a must for a successful signup. Since a bot is creating an account successfully, it is obvious that CAPTCHA is broken.
Here is a closer look at the series of actions during the entire process by carefully investigating the network traffic:
We discovered that the CAPTCHA breaking process for Gmail is sophisticated when compared to the Live Mail CAPTCHA break up which was reported in our recent blogs.
Here are our findings
Consider the figure included below:
It is observed that two separate hosts active on same domain are contacted during the entire process. These two hosts work collaboratively during the CAPTCHA break process. Unlike Live Mail CAPTCHA breaking, which involved just one botted host doing the entire job (signing up, filling in details, getting the CAPTCHA request), the Gmail signing process involves two botted hosts (or CAPTCHA breaking hosts).
In this case, Gmail involves two hosts with different CAPTCHA breaking processes. Why? Because of variations included in the Google CAPTCHA image, chances are that host 1 may fail breaking the code. Hence, the spammers have a backup or second CAPTCHA-learning host 2 that tries to learn and break the CAPTCHA code. However, it is possible that spammers also use these two hosts to check the efficiency and accuracy of both hosts involved in breaking one CAPTCHA code at a time, with the ultimate goal of having a successful CAPTCHA breaking process.
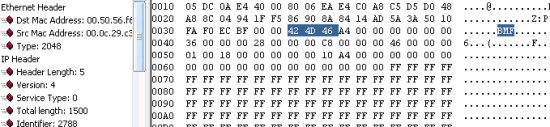
To be specific, host 1 has a similar concept that was used to attack Live mail CAPTCHA. This involved extracting an image from a victim’s machine in the form of a bitmap file, bearing BM.. file headers and breaking the code. Host 2 uses an entirely different concept wherein the CAPTCHA image is broken into segments and then sent as a portable image / graphic file bearing PV..X file headers as requests.
From this complicated process it is obvious that Google’s CAPTCHA is a bit tougher challenge to spammers. But they still seem to have a certain level of success working with different CAPTCHA breaking concepts.
Process in action
Part 1: Communication with host 1
From the above figures, it is observed that the bot-infected machine communicates with host 1 during the process.
Once the bot opens the Gmail mail page and is ready to sign up, the bot starts filling in credentials and when it comes to CAPTCHA, the breaking requests are sent as shown below:
Observe the CAPTCHA image break request sent:
Observe the CAPTCHA code as a reply:
The CAPTCHA authentication code is received, and the account is success fully created. Note: Here the whole image is sent at once in the form of a bitmap file for breaking.
Part 2: Considering communication with host 2
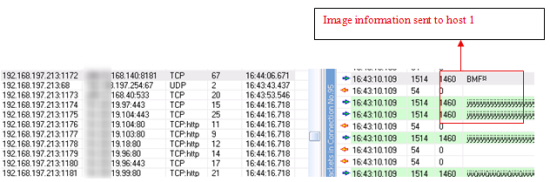
It is observed that the image information is sent to host 2 in a number of parts. This indicates that the image is broken into segments and then sent to the CAPTCHA breaking server for code request. The code is received back or replied to after each segment request as shown in the figure below:
Example of segmented requests - Request 1:
Replies from CAPTCHA breaking host:
Observe that first character determined by first CAPTCHA breaking process (involving host 1), as mentioned above, was indeed “n”. Thus, segment by segment the requests are sent and answers are received.
However, it observed that the other request fails, as shown below:
No value of the image segment is received. Therefore, the second host fails to complete breaking the CAPTCHA code.
Depending upon the number of segments, the requests are continued and codes are determined. This is carried out in a sequential manner every time to guess the possible answer.
Observe the links visited by the bots in the background:
Observation*: On average, only 1 in every 5 CAPTCHA breaking requests are successfully including both algorithms used by the bot, approximating a success rate of 20%. The second algorithm (segmentation) has very poor performance that sometimes totally fails and returns garbage or incorrect answers.
Additional information
It is observed that a wide range of dedicated CAPTCHA breaking services are hosted on a pro-active domain located in the US.
A few other things
Observations on CAPTCHA breaking host 1:
- It is observed that host 1 contains a single page with Russian text on it:
In English it reads as:
FAQ
If you are unable to recognize a picture or she is not loaded (picture appears black, empty picture), just press Enter.
In no case do not enter random characters!
If there is delay in downloading images, exit from your account, refresh the page and go again.
The system tested in browsers:
Internet Explorer
Mozilla Firefox
Before each payment deemed by pictures checked Admin. We pay only correctly recognized pictures!
The payments are made to 1 time per day. The minimum amount to be paid $ 3. To have ordered the payment, send in their application consisting of admin. If the administrator is free, your application will be processed within 10-15 minutes, if it is busy as possible.
If you have any problems (issues) knock Admin.
The very look of the home page (as shown above) clearly indicates that this entire service is dedicated to breaking CAPTCHA, with an obvious aim to make money out of it.
2. We discovered a page hiding inside host 1, which appears to be an internal test page to test the CAPTCHA breaking process.
3. We tested and observed that this page accepts only bitmap files as input. We discovered that the network traffic resembles the observed traffic during the CAPTCHA breaking process while CAPTCHA image break requests are sent from bots or bot-infected machines. Observe our test results:
4. We also discovered that test pages were hidden on separate hosts within the same IP range on this domain.
Observe the page that comes up when this IP is visited:
Further, we discovered a page hiding within this host, which appears to be another internal test page to test the accuracy of the CAPTCHA breaking process internally, as shown:
This test page appears to be similar to the previous test page discovered, but has an additional text input field. This appears to be a test page that is used internally for testing the CAPTCHA code with the corresponding image. However, the results are obtained and tested internally, as the page resolves in an error after the inputs are fed to it.
We believe that all the hosts on this domain are dedicated to CAPTCHA breaking services. After careful observation and investigation at different levels during the entire process, we believe that the same group is involved in the Live Mail CAPTCHA break and also Gmail CAPTCHA break processes.
Note: For more information on Gmail, see the Gmail entry on wikipedia.org.



















没有评论:
发表评论